Blog Posts

- Altacom
- Bitdefender

Authentication in Zero Trust
Zero Trust has proved itself to be an effective strategic cybersecurity model for the protection of critical data and systems. The system components in a Zero Trust (ZT) architecture, which by default do not trust and deny access requests, and each node of the network or system is authenticated, authorized, and continuously validated as a part of this concept.

State of Symmetric & Hash Algorithms after Quantum Computing
The recent trends in information technology and communications have emerged as one of the main technological pillars of the modern age. The importance of cryptography has gained importance due to the requirement of security services (confidentiality, integrity, authenticity, and non-repudiation) in data storage/transmission.

Understanding the Role of Hardware Security Modules in Digital Identities for Humans
eIDAS created standards for trust services to ensure that digital identities, including those for humans remain secure with the presumption of integrity, and are exclusively linked to the individual, entity, or machine through cryptographic protections.

Secure Transactions with eIDAS
Under eIDAS, the EU aims to facilitate cross-border digital transactions and pave the way for a Digital Single Market. Qualified electronic signatures and seals play a decisive role with this goal. Thanks to eIDAS, users can obtain both as a service via remote signing/sealing as well.

eIDAS 2.0 - Introduction to The European Digital Identity Wallet & The Evolution of Self-Sovereign Identity
In June 2021, the European Commission proposed an update to its pan-European digital identity framework. It will enable every European to have a set of digital identity credentials that are recognized all across the EU – otherwise known as European Digital Identity (EUDI) Wallets.

Qualified Signature Creation Devices (QSCD) under eIDAS – The example of the Bank-Verlag Signature Activation Module (SAM)
eIDAS requires a Qualified Signature (or Seal) Creation Devices (QSCD) for issuing and using qualified certificates for the generation of electronic signatures and seals. Today we would like to look into how the CC-certified and eIDAS-compliant Utimaco HSM integrates with the Bank-Verlag Signature Activation Module (SAM) and helps Bank-Verlag become a TSP.

Understanding and planning for a post-quantum security ecosystem
By now, we hope that you understand that, sooner or later, your company will have to become quantum secure. In 2021, IBM announced ‘Eagle’, a working quantum computer with 127 quantum bits (or ‘qubits’) followed closely on the heels of China’s announcement of two quantum computers.

NIST Digital Identity Guidelines & Identity Proofing - Why Using A Public Key Infrastructure Is A Key Requirement
Every person and “entity” (computers, smartphones, internet-connected devices (IoT), applications and further endpoints) in today’s digital environment has a unique digital identity. A digital identity contains certain unique identifiers that allow systems, services, and applications to know who or what they are interacting with.

Local vs. remote signing and sealing according to eIDAS
One of the eIDAS objectives is the creation of a European market for electronic trust services with the same legal status and validity as paper-based processes – consistently applied across all member states.
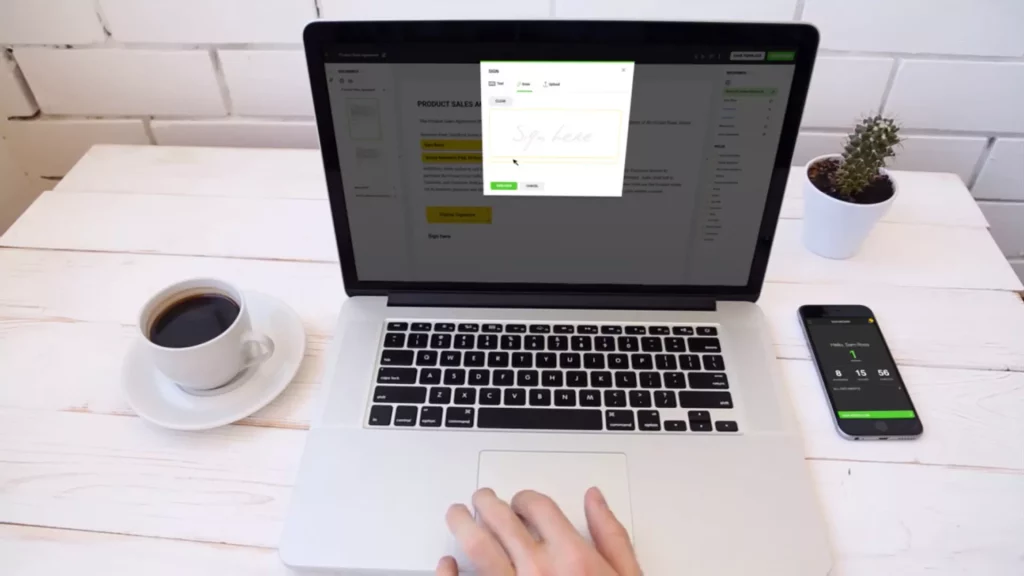
A new era for e-signatures – how eIDAS is shaping the future of high-trust signing
eIDAS has helped herald a new era of e-signing for businesses operating across Europe. E-signatures provide a fast, secure, efficient and cost-effective alternative to paper signing and the eIDAS regulation ensures legal certainty across the EU with its requirements for Basic, Advanced and Qualified e-signatures.

eIDAS: The Advantages of QES as compared to AES
Advanced and Qualified Electronic Signatures are electronic signatures that comply with EU Regulation 910/2014 on eIDAS electronic transactions in the European internal market. They enable long-term verification of electronic signatures. Today, we explain the difference between Qualified and Advanced Electronic Signatures, both in terms of legal status and technical requirements.

An Introduction to the Regulatory Technical Standards for Strong Customer Authentication – Part 3: Achieving Transactional & Account Security
The Regulatory Technical Standards (RTS) is a supplementary directive designed to complement the Revised Payment Service Directives (PSD2), eIDAS and any other such cases where Strong Customer Authentication is required.

An Introduction to the Regulatory Technical Standards for Strong Customer Authentication – Part 2: PSD2
The Revised Payment Service Directive (PSD2) is nothing short of revolutionary when it comes to the retail payment services industry in Europe. In fact, many of the innovative new products and services that PSD2 will indirectly create are likely to percolate to every sector of the economy.

An Introduction to the Regulatory Technical Standards for Strong Customer Authentication – Part 1: eIDAS
A major challenge faced by the EU in the creation of a Digital Single Market is finding the right balance between processes that can be harmonized and standardized and those that need to remain flexible to cater to the demands of the various Member States.

Bitdefender Threat Debrief | October 2023
Even as October’s Cybersecurity Awareness Month floods the internet with articles and campaigns about the importance of online safety, we’ve observed a surprising increase in user-driven security incidents. This is especially alarming because one would expect such incidents to decline, rather than spike, during a month dedicated to cybersecurity education.

Bitdefender Threat Debrief | August 2023
In our previous discussion about Threat Modeling and its application in Bitdefender MDR’s intelligence monitoring, we emphasized the importance of considering the threat landscape. This term refers to the overall picture of potential cybersecurity threats and risks faced by individuals, organizations, or systems, including various cyberattacks, vulnerabilities, and potential adversaries.

4 Key Industries That Need to Prioritize Cybersecurity
The cybersecurity industry is undergoing a significant shift as it’s finding its way to adapt to a post-pandemic world. Over the past few years, industries accelerated their digital transformation efforts, increased their reliance on remote work, and leveraged cloud-based services on a greater scale.